Streamlining Mobile App Security in the SDLC with Ostorlab
Integrating a sophisticated mobile security platform into the Software Development Life Cycle (SDLC) provides teams with the tools to identify, remediate, and manage security threats effectively.
Ostorlab platform, equipped with varied scanning profiles, CI/CD integration, training, remediation tracking, and an integrated debugging environment (IDE) for incident handling, offers a comprehensive security toolkit.
Here’s how you can incorporate these features throughout the SDLC:
1. Planning Phase
Security Training and Awareness:
Utilize the full scanning capabilities of the platform to establish robust security benchmarks.
To augment this process, use the security dashboard provided by the platform. This dashboard, along with its metrics, will be instrumental in tracking scanning frequency, identifying trends in vulnerabilities, and monitoring the progress of remediation efforts. This visibility is essential for maintaining an agile and responsive security posture throughout the development lifecycle.
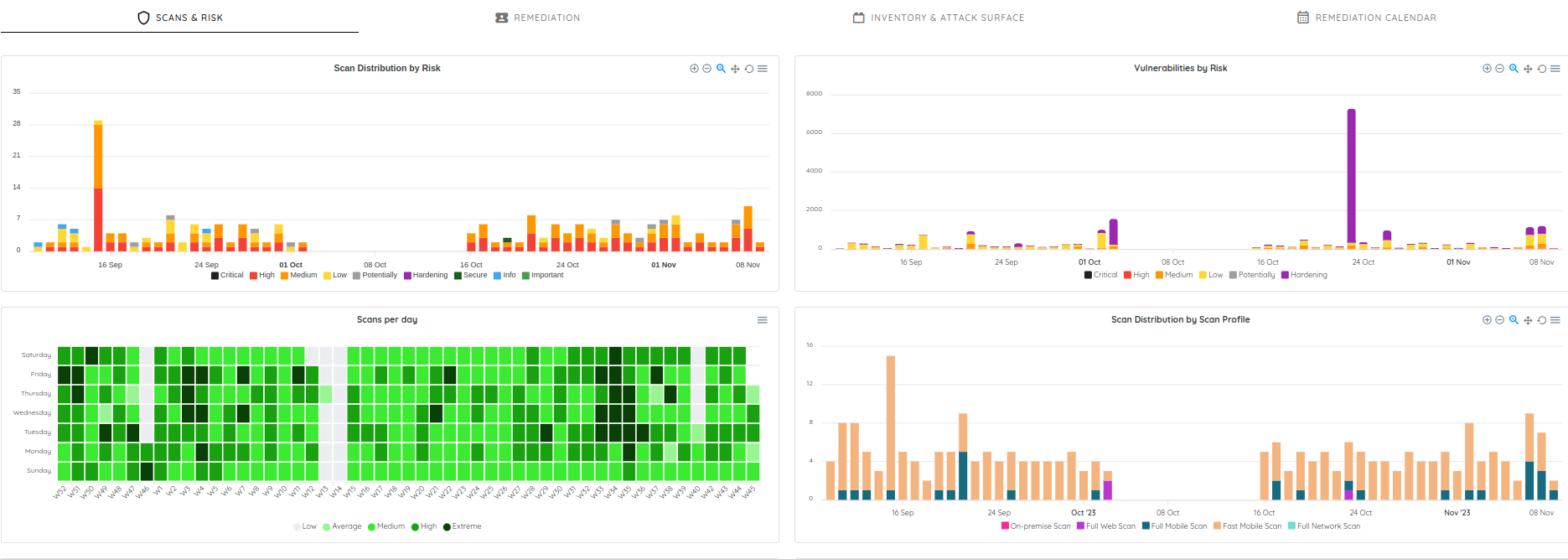
For more details check the link: https://docs.ostorlab.co/guide/dashboard/overview.html
By incorporating these proactive measures in the planning phase, an organization can establish a strong foundation for mobile application security that permeates the entire SDLC.
Security Policy and Benchmarking:
Harness the full scanning capabilities of the platform to define your application's security benchmarks. Formulate a clear patching policy that articulates the process for timely remediation of vulnerabilities.
Enhance these efforts with the platform’s security dashboard and metrics, which allow for effective tracking of scan frequencies, vulnerability trends, and remediation progress. These tools are vital for sustaining an adaptive security approach throughout the product’s lifecycle.
2. Design Phase
Security by Design:
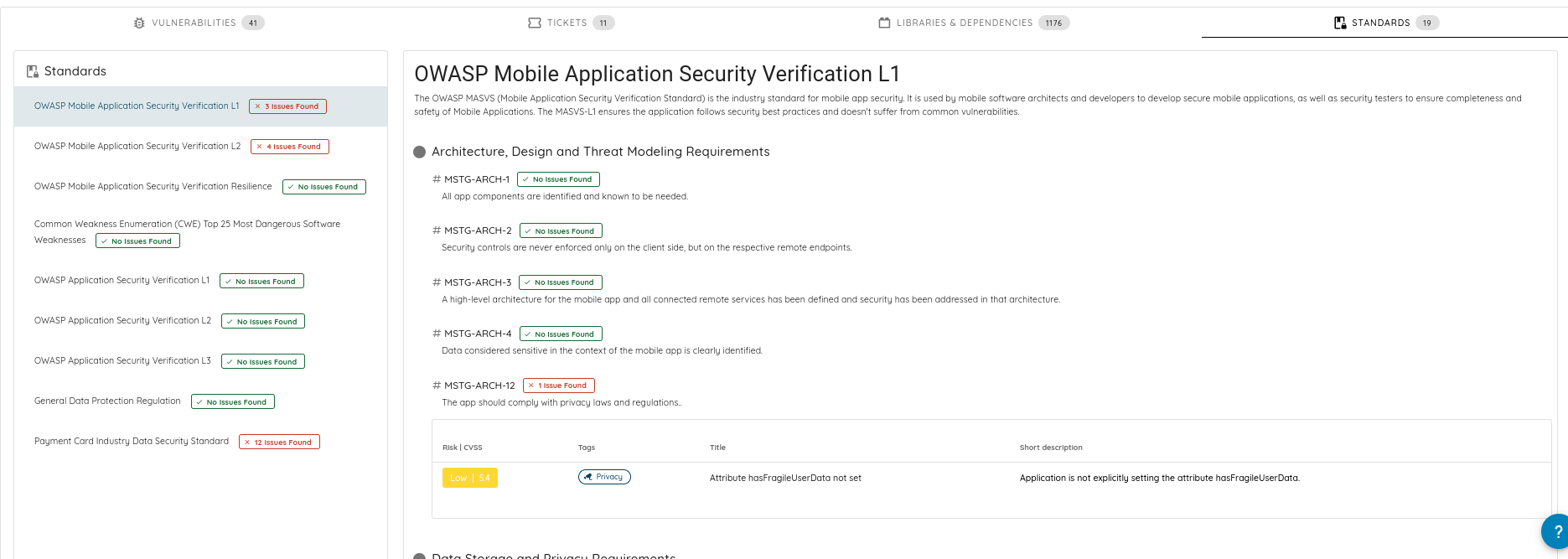
Embed security into the application's architecture using the platform's comprehensive scan results. Ensure that the design mitigates known vulnerabilities and aligns with best practices outlined in the standards section of the scans, which includes references to the OWASP Mobile Security Testing Guide. This guide is crucial for understanding the security aspects that should be incorporated during the design phase.
Link to documentation: https://docs.ostorlab.co/tutorials/generate_pdf_report.html
Threat Modeling:
Incorporate threat modeling to anticipate and strategize against potential security threats, utilizing the platform to provide insights into prevalent risks for mobile applications. Specifically, references OWASP Threat Modeling, a methodology that offers a structured approach for identifying and addressing security threats. This reference will ensure that your threat modeling is aligned with industry-standard practices and that the design is fortified against potential security challenges.
By weaving these targeted security measures into the early stages of the SDLC, organizations can create a solid foundation that promotes the development of secure mobile applications. Integrating the OWASP Mobile Security Testing Guide and Threat Modeling into the design phase ensures that security is not just an add-on but a fundamental component of the application's design.
3. Development Phase
Secure Coding Practices:
It's crucial for developers to adhere to secure coding practices to ensure the integrity and safety of the application. To support this, provide ongoing access to the platform’s educational resources to foster continuous improvement. Additionally, developers should be directed to the platform's Knowledge Base (KB), which offers a wealth of examples of vulnerabilities to avoid. This reference material can serve as a practical guide for writing more secure code, helping developers understand the nuances of common security pitfalls and how best to sidestep them. By integrating these resources into the development workflow, secure coding practices become a natural part of the development process rather than an afterthought.
CI/CD Integration with Fast Scanning:
Embed the platform's fast scanning profile within the CI/CD pipeline. This ensures each code commit is checked for vulnerabilities, enabling real-time feedback and immediate remediation without slowing development cycles.
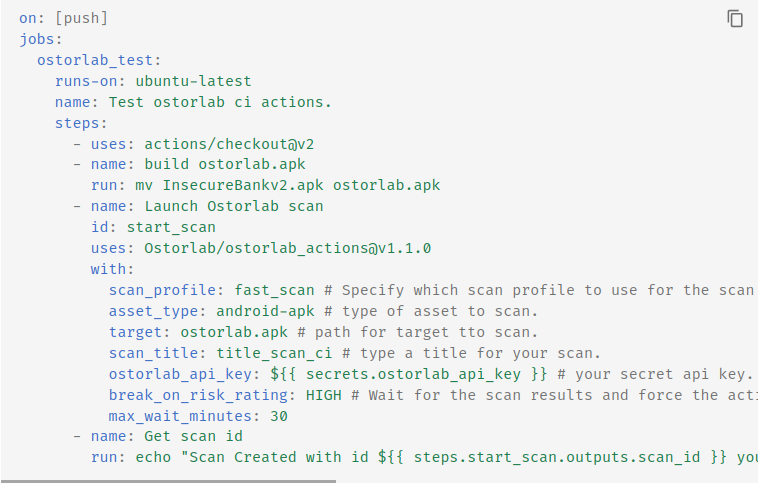
For more details check the link: https://docs.ostorlab.co/integrations/github/index.html
Remediation Workflow:
Utilize the platform's remediation capabilities to track and manage fixes. This feature should help developers prioritize issues based on severity and align with the patching policy outlined in the planning phase.
![]()
For more details check the link: https://docs.ostorlab.co/remediation/index.html
4. Testing Phase
Comprehensive Pre-Release Scans:
Run the platform's full scan before every release to ensure a thorough security check. Even without a dedicated penetration testing phase, this rigorous scan uncovers any critical issues that must be addressed. Ensure to utilize the platform's authenticated scan capabilities, which perform a deeper analysis by scanning through authenticated sessions. This can reveal vulnerabilities that are not visible during unauthenticated scans, such as issues within user accounts or administrative interfaces. Authenticated scans are essential for a full evaluation of the application's security posture before it goes live.
For more details check the link: https://docs.ostorlab.co/authenticated_scans/index.html
Automated Regression and Security Testing:
Incorporate automated security tests, including regression testing, into the CI/CD process, ensuring that past vulnerabilities continue to stay patched in new builds.
For more details check the link: https://docs.ostorlab.co/integrations/github/index.html
5. Deployment Phase
Deployment Readiness:
Conduct a final full scan using the platform to validate that the application is secure and adheres to the security benchmarks before production deployment.
For more details check the link: https://docs.ostorlab.co/tutorials/mobile_store_scan.html
Secure Release Practices:
Follow the security platform’s guidelines for a secure deployment, minimizing risks associated with the release process.
For more details check the link: https://docs.ostorlab.co/mobile_application_security_testing/index.html
6. Maintenance and Operations Phase
In-Store Monitoring and Response:
Deploy the platform’s monitoring solutions to watch over the deployed application, particularly for detecting security issues in real-time as the app operates in the wild.
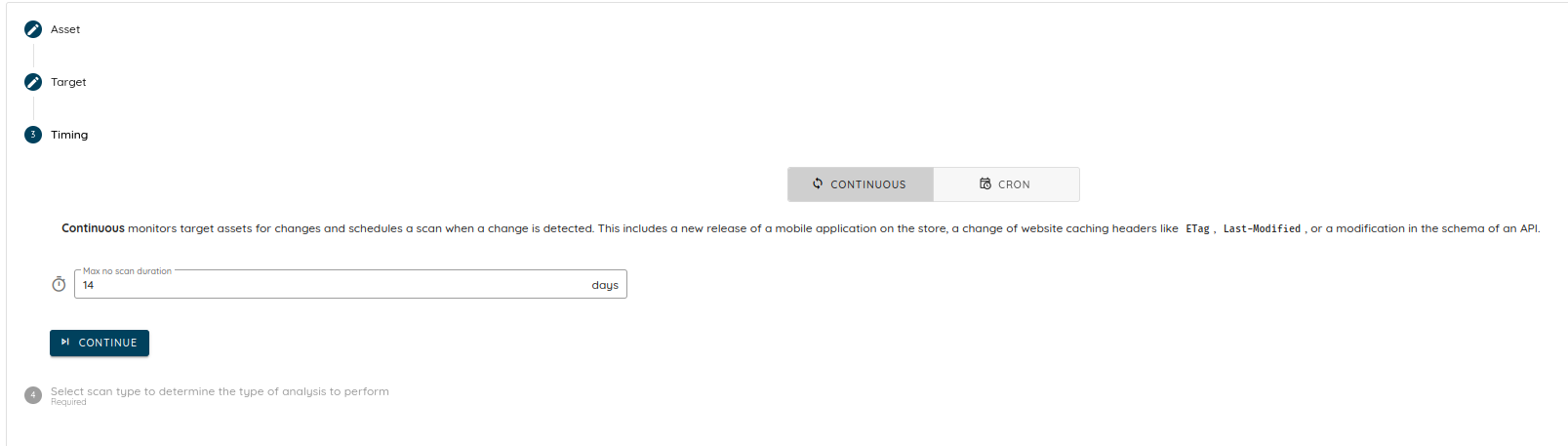
For more details check the link: https://docs.ostorlab.co/monitoring/index.html
Remediation and Incident Response:
Should a security incident occur, utilize the platform’s IDE to investigate and respond to issues swiftly. This environment aids developers by providing the context and tools needed for an effective incident response.
For more details check the link: https://docs.ostorlab.co/ide/index.html
Continuous Security Posture Improvement:
With each full scan and the ongoing feedback from the monitoring tools, continuously refine and enhance the security measures of the mobile application.
For more details check the link: https://docs.ostorlab.co/guide/dashboard/overview.html
Patch Management and Tracking:
Adhere to the established patching policy, using the platform's tracking capabilities to ensure timely and consistent application of fixes and updates.
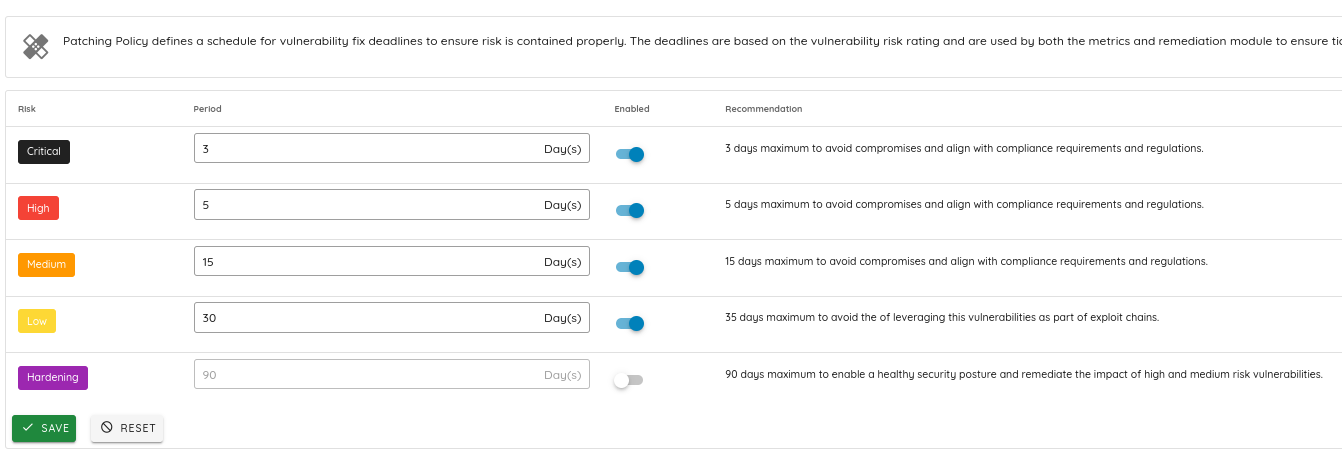
For more details check the link: https://docs.ostorlab.co/tutorials/config_Patching_Policy.html
Conclusion
By leveraging the full suite of capabilities offered by a dedicated mobile security platform, organizations can instill a robust security posture at every phase of the SDLC. The integrated training, scanning, remediation, and monitoring tools not only streamline the process of securing mobile applications but also empower developers to tackle security issues proactively. This comprehensive approach ensures that mobile security is an integral and efficient part of the mobile application development process, delivering secure applications that stand up to the threats of the digital world.