Detection
Ostorlab scanning capabilities use static analysis for high coverage of the attack surface and dynamic analysis for false-positive free reports. Ostorlab targets system backends collected during dynamic analysis to identify server-side vulnerabilities.
Static Analysis
Ostorlab’s Static analysis uses multiple techniques to identify vulnerabilities:
Configuration Checks
Configuration checks for insecure settings. These settings include Android and iOS native parameters, like
AndroidManifest.xml debug and backup mode, Cordova Framework parameters, like Cordova whitelist or debug mode.
For a full list of checks, see knowledge database section.
3rd Party Dependencies
3rd Party dependencies fingerprint all the application dependencies of all supported frameworks, like native Android, iOS Cocoapods Cordova Plugins, Xamarin DLL ...
The 3rd Party dependencies also fingerprint statically compiled dependencies and identify a large set of libraries like OpenSSL, Zlib, Libjpeg, Libpng, Xerces ....
The fingerprints are matched against the known vulnerabilities database. The database contains both publicly reported vulnerabilities, and a list of non-reported vulnerabilities identified by analyzing public source code repositories.
The vulnerability database is accessible at the VunlDB menu and can be used to search for entries by date, name and version.
Hardcoded Secrets
The static engine searches for hardcoded secrets, like API Keys that shouldn't be deployed in a mobile application, as well as passwords, tokens and encryption keys and IV.
Identified secrets are tested for validation and impact by checking permissions, roles and accessible services.
Taint Analysis
Ostorlab’s core static technology is its taint engine that computes how taints propagate over several possible execution paths. Ostorlab’s static taint engine takes into account object-oriented information and typing information to offer fast, efficient and near false-positive-free taint info. Dozens of rules then use the taint info to identify vulnerabilities, like SQL injection, command injection, or the use of hardcoded keys.
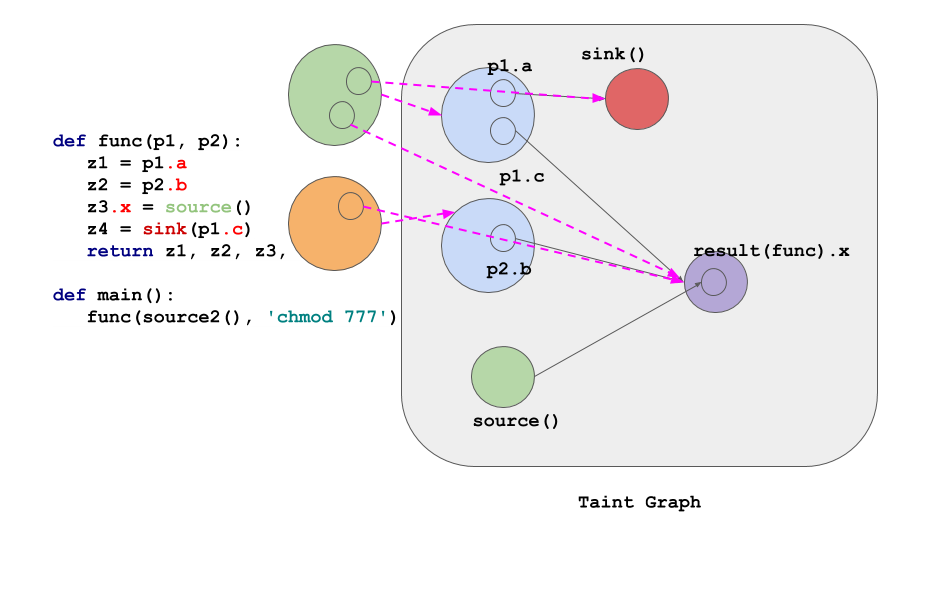
Dynamic Analysis
Ostorlab runs mobile applications in an instrumented sandbox to track all interactions with the external environment, like network, filesystem, keychain, API, etc.
The instrumentation engine tracks calls to standard APIs to identify unsafe arguments, like weak encryption schemes, unsafe RPC calls, code loading from untrusted paths or command execution with user input.
Ostorlab instrumentation can access encrypted traffic and does not require bypassing SSL pinning. The collected backend is then reused to perform backend analysis.
The dynamic instrumentation uses both system instrumentation techniques, like Fanotify for file system access and a custom non-pervasive runtime instrumentation engine, using JDWP and debug APIs for Android and iOS.
This approach compared to pervasive methods, like inline hooking that requires custom memory manipulation is very robust offers more capabilities to collect runtime information, particularly for iOS applications built using Objective C and Swift and don’t require constant maintenance with every new system release that may bring modification to the underlying system runtime.
Backend
Ostorlab targets collected backends during dynamic analysis to identify server-side vulnerabilities. The analysis is both passive, like detecting the presence of insecure HTTP headers as well as active, like detecting SQL injection or XXE.
Ostorlab uses an advanced Cross-Site Scripting (XSS) scanner agent with dynamic Chrome-based testing and powerful polyglot payloads. The scanner also uses methods like integration of JavaScript Proxy object instrumentation into the preliminary profiling of web applications to streamline the detection of nuanced XSS vectors.
Ostorlab's active testing uses a probabilistic approach to identify vulnerabilities. This approach has the advantage of avoiding the need to send a full payload which could be blocked, limited to a particular OS, may impact the backend stability or trigger intrusion detection systems or application firewalls.
In addition, Ostorlab automates the detection of critical, high-severity, and actively exploitable vulnerabilities sourced from reputable platforms like CISA's KEV, Google’s Tsunami, and the innovative Ostorlab’s Asteroid Project.
Ostorlab backend analysis engine supports a large set of serialization schemes and supports nested serialization injection.
Probabilistic testing coupled with safe rate-limiting protects backend systems from unexpected failures and unwanted denial of service and offers guaranteed false positive free reports.