GoCD
Easily integrate Ostorlab automated security scanning for Android and iOS mobile applications into your GoCd build process.
Usage:
Generate an Ostorlab API key
- Go to the API keys menu
- Click the new button to generate a new key
- Copy the API key (You can add a name and an expiry date to your key)
- Click the save button to save your key

Add Ostorlab as a Command Line Stage on GoCd
-
Head to your
GoCdDashboard and select your pipeline.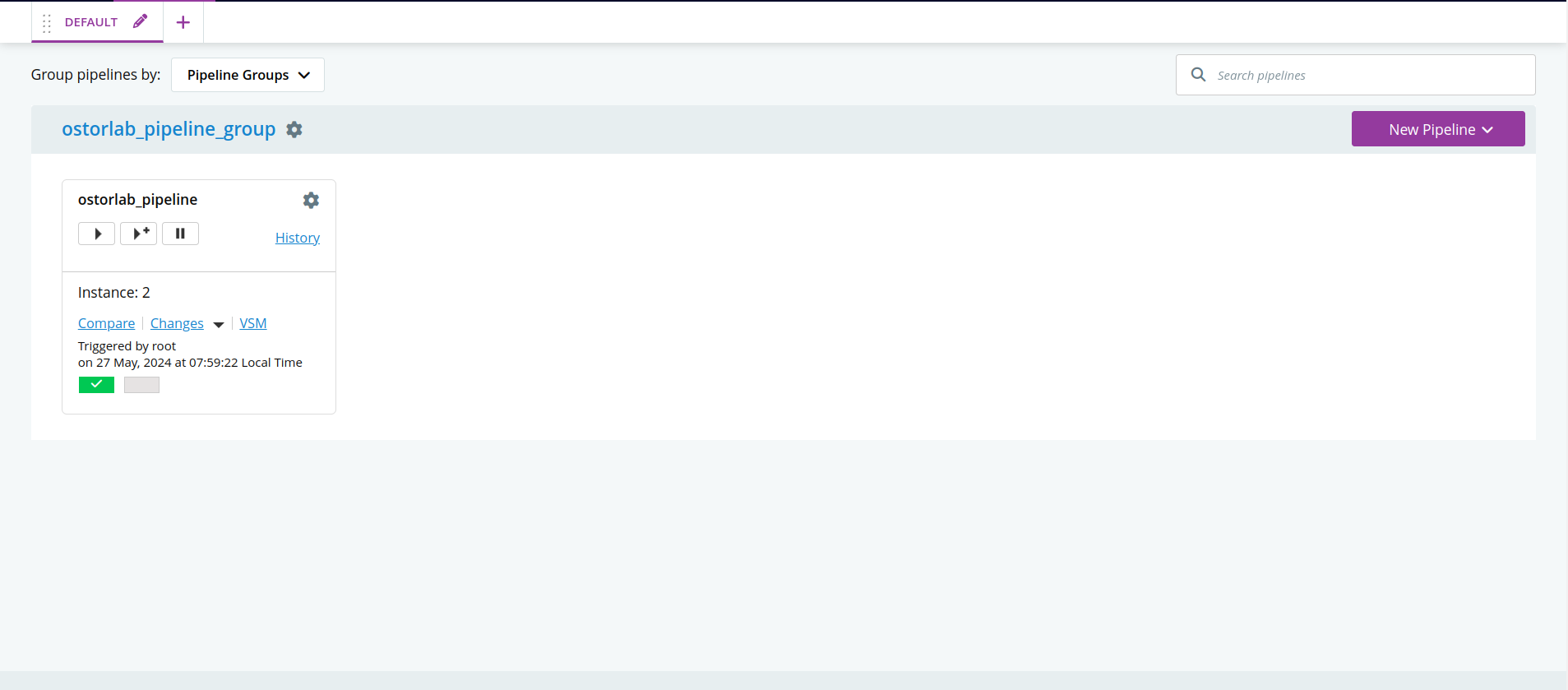
-
Click
Editon your pipeline.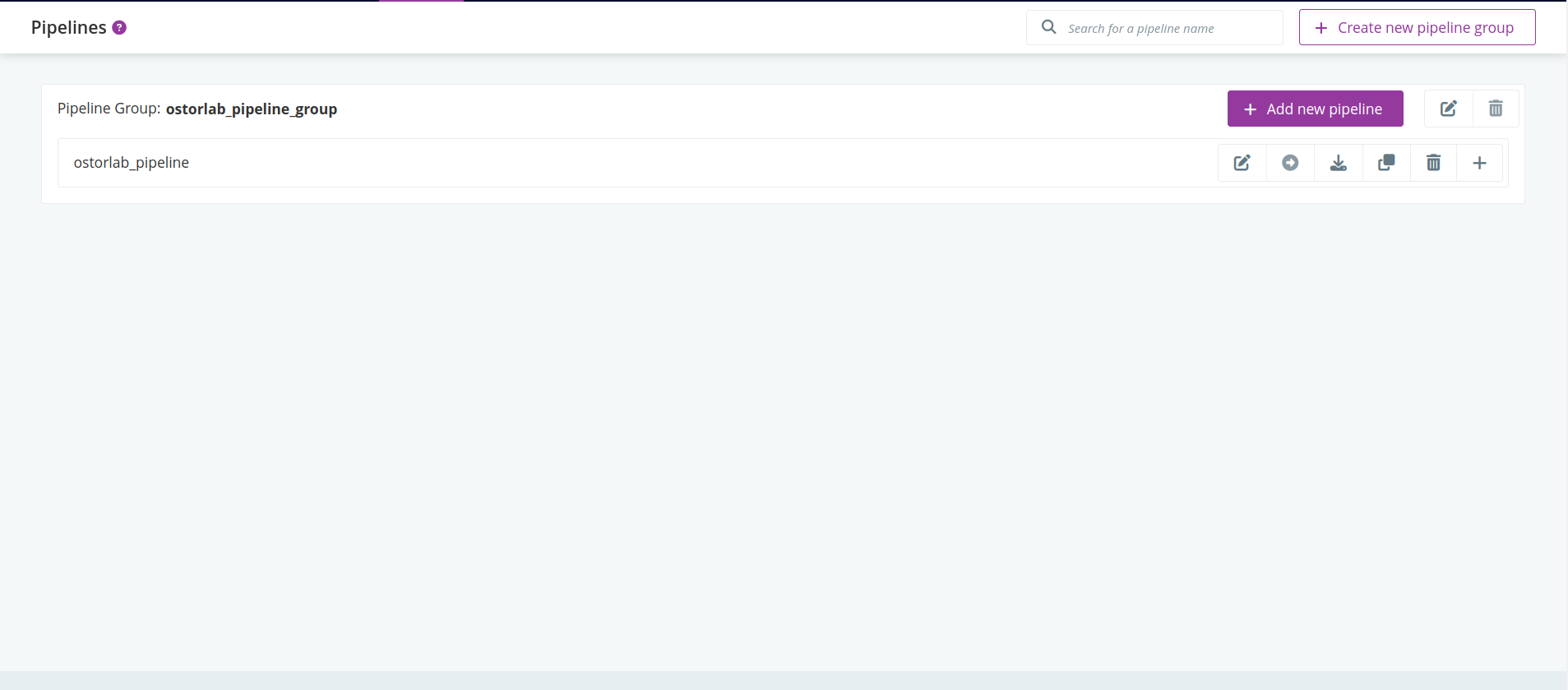
-
Select Stages.
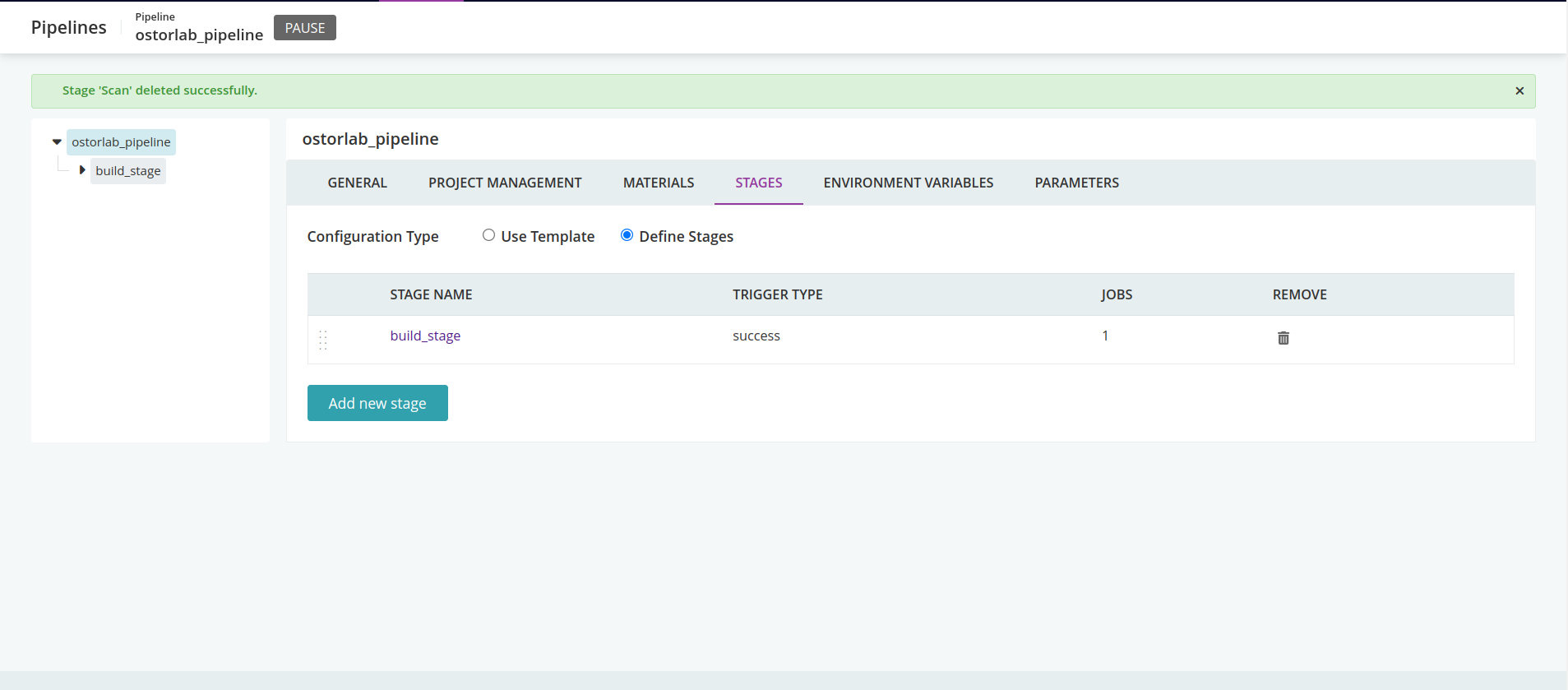
-
Add new stage and fill the form.
- For the initial Job type Select
Custom Command. - And give it the following arguments:
Command:bashArguments: |-c pip install ostorlab- click save.
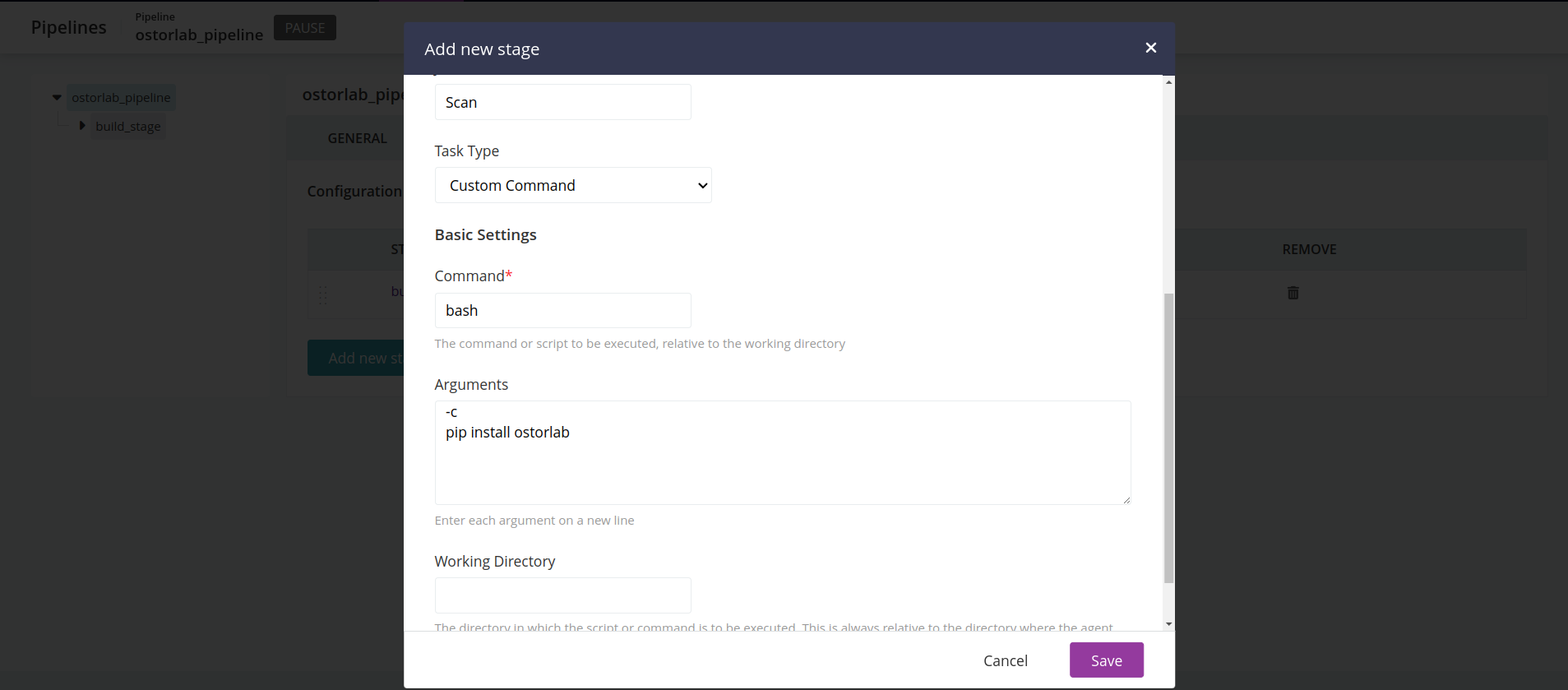
- For the initial Job type Select
-
Navigate to
JOBStab and select your newly added job.
-
Add one more task to run the job.
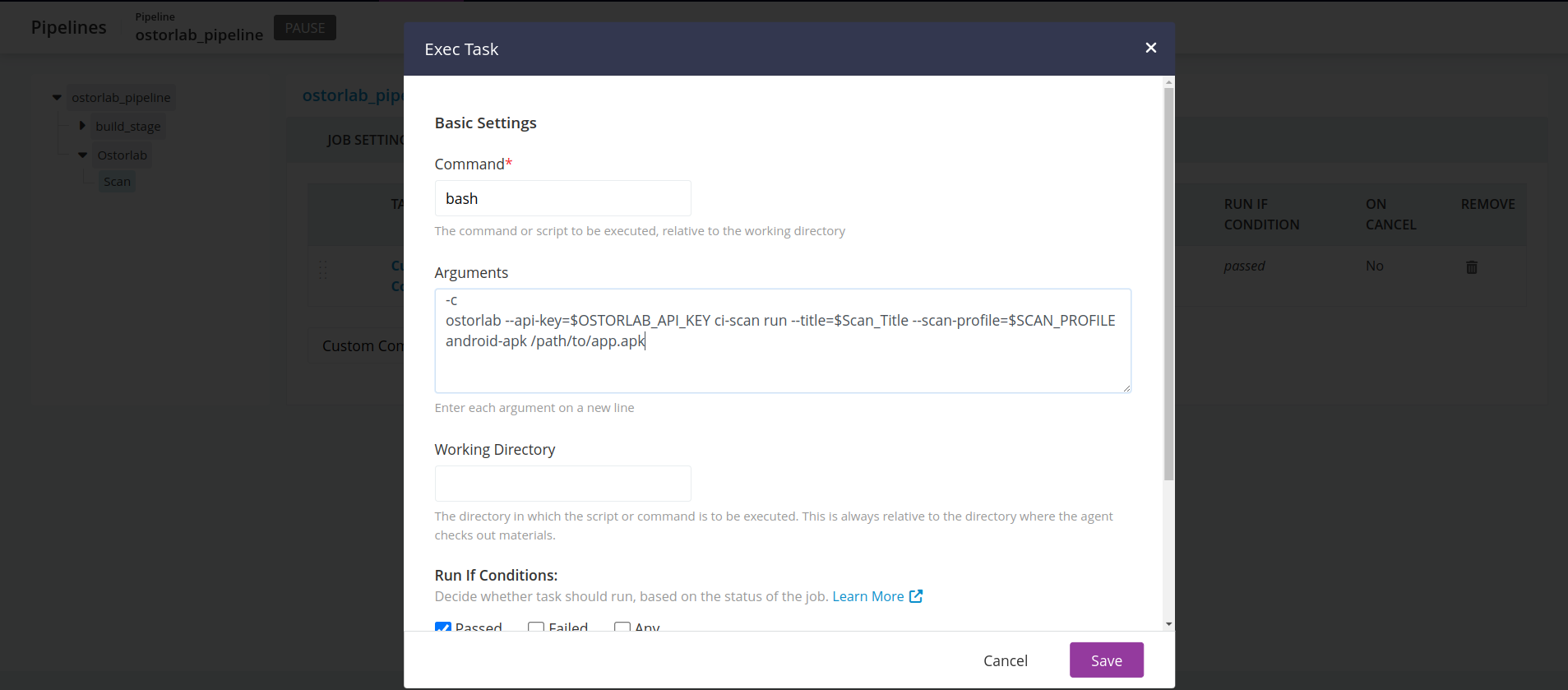
- Click add Task of type
Custom Command. - And give it the following arguments:
Command:bashArguments: |Check-c ostorlab --api-key=$OSTORLAB_API_KEY ci-scan run --title=$Scan_Title --scan-profile=$SCAN_PROFILE android-apk /path/to/app.apkAdditional optionsbelow for the full list of options.
- Click add Task of type
-
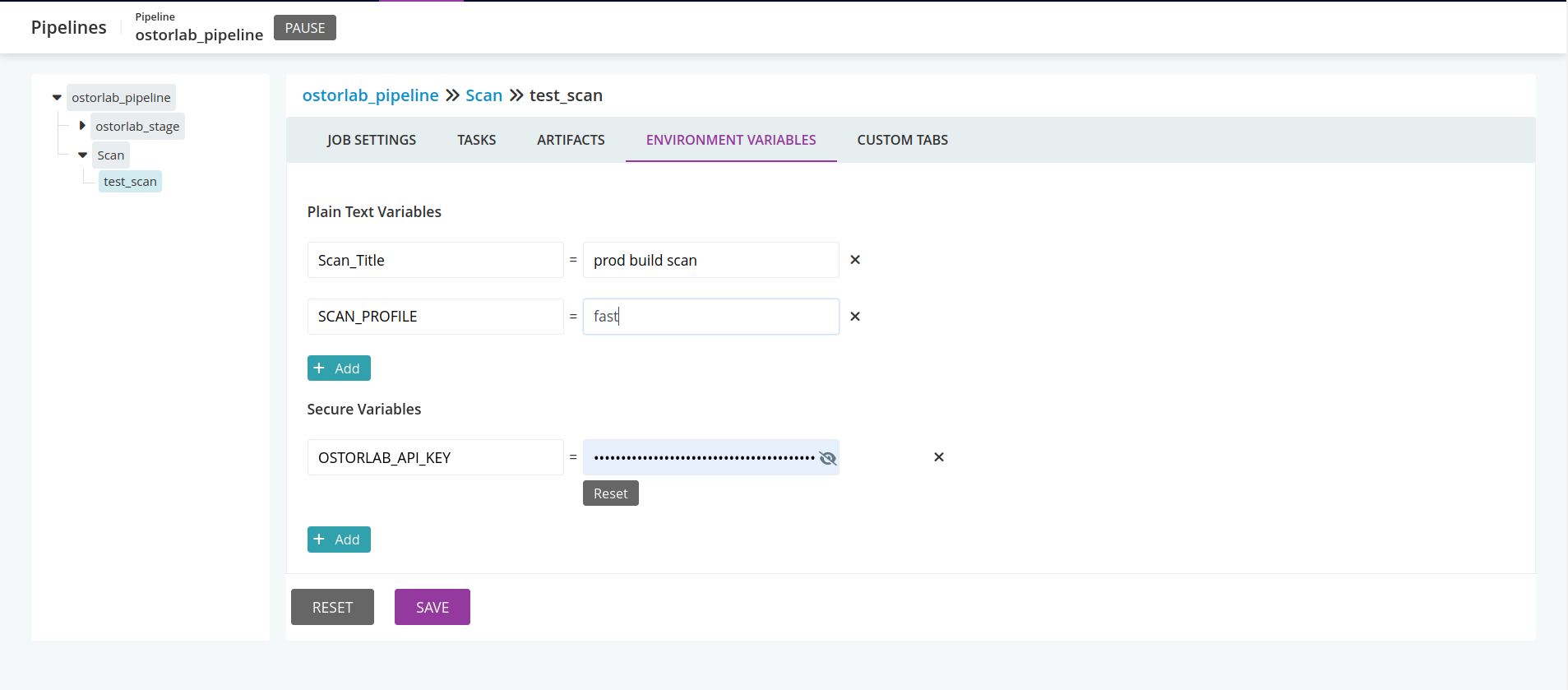
Add environment variables
- Navigate to the
ENVIRONMENT VARIABLEStab. - Add the
OSTORLAB_API_KEYas aSecure Variable. - Add the other variables (Scan_Title, SCAN_PROFILE, ...) as
Plain Text Variables.
- Navigate to the
Additional options
The following is the full list of options for the ostorlab ci-scan run command:
ostorlab --api-key ci-scan run --option <asset-type> <target>
-
--api-key: Ostorlab generated API key.
-
--title: Scan title
-
--scan-profile: Type of the scan. Possible options are:
fast_scan: Only runs the static analysis;full_scan: Runs static, dynamic, and backend analysis.
-
Test credentials: Automatic authentication in the dynamic analysis full scan:
- --test-credentials-login: Username to be used in log-in fields;
- --test-credentials-password: Password to be used in password fields;
- --test-credentials-role: Optional role field;
- Custom/Generic test credentials:
- --test-credentials-name: Custom name of the field;
- --test-credentials-value: Custom value of the field
-
--sbom: Path to the sbom file.
-
UI Prompts (Optional): Ostorlab supports UI prompts to guide the scanner through your app's user interface. You can use:
- --ui-prompt-name and --ui-prompt-action: Define a UI step by specifying the name and the action. You can add multiple pairs for a sequence of steps. For example:
--ui-prompt-name accept-terms --ui-prompt-action "Scroll down and tap the 'Accept Terms' checkbox." --ui-prompt-name submit --ui-prompt-action "Tap the 'Submit' button to complete the login process." - --ui-prompt-id: Reference existing UI prompt flows by their IDs. You can add multiple IDs. For example:
--ui-prompt-id 123 --ui-prompt-id 456
- --ui-prompt-name and --ui-prompt-action: Define a UI step by specifying the name and the action. You can add multiple pairs for a sequence of steps. For example:
-
asset-type: Type of the asset to scan. Possible values:
android-aab: Scan an android.AABpackage file;android-apk: Scan an android.APKpackage file;ios-ipa: Scan an iOS.IPApackage file;
-
target: Path to the target application.