Monitoring
Welcome to this guide on how to manage monitoring rules
Monitoring section located in the left menu.
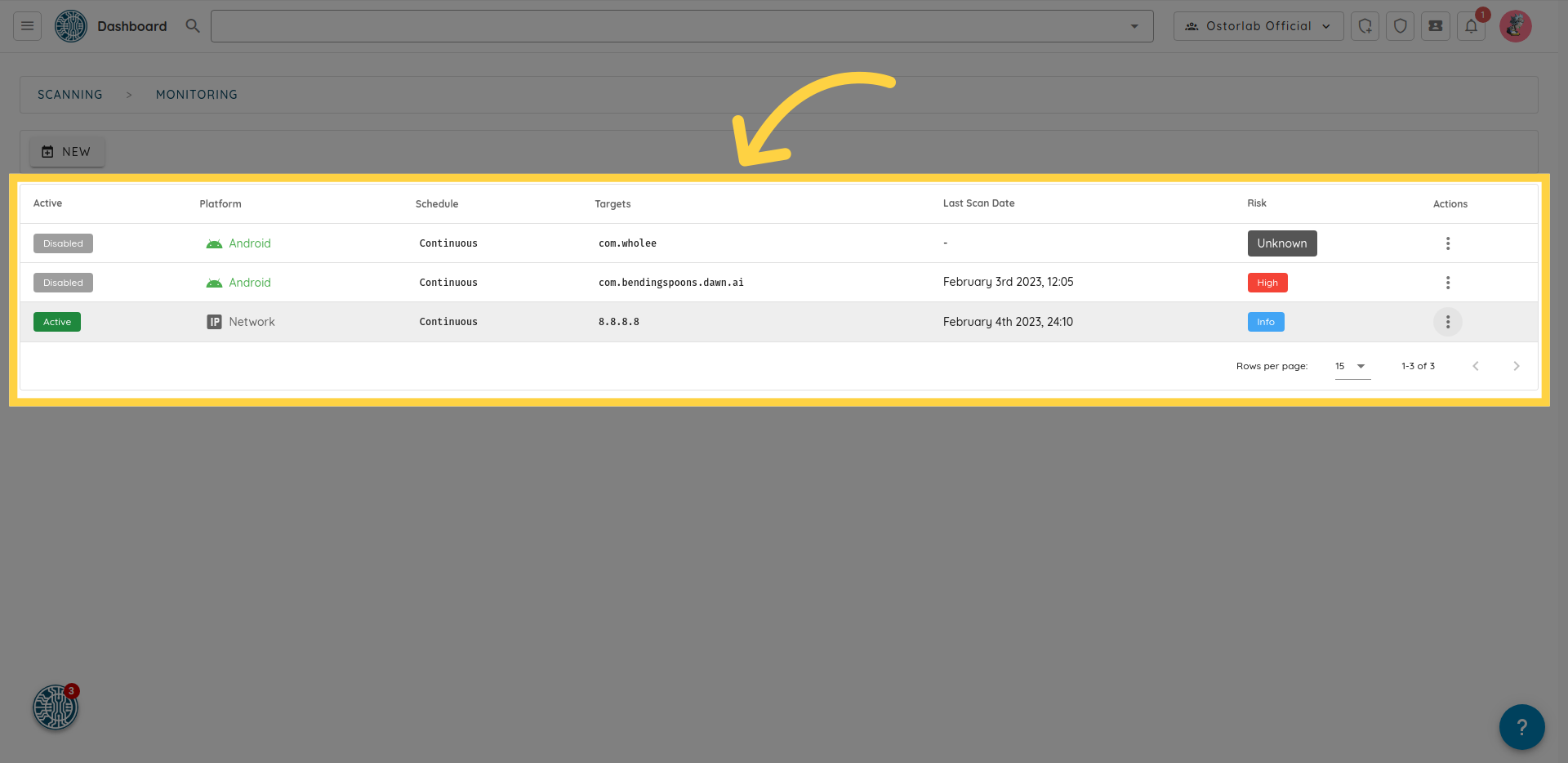
here, you can see all of your monitoring rules, including the assets being monitored, the date of the last scan, the risk rating of the last scan, and the status of each rule, if enabled or disabled.
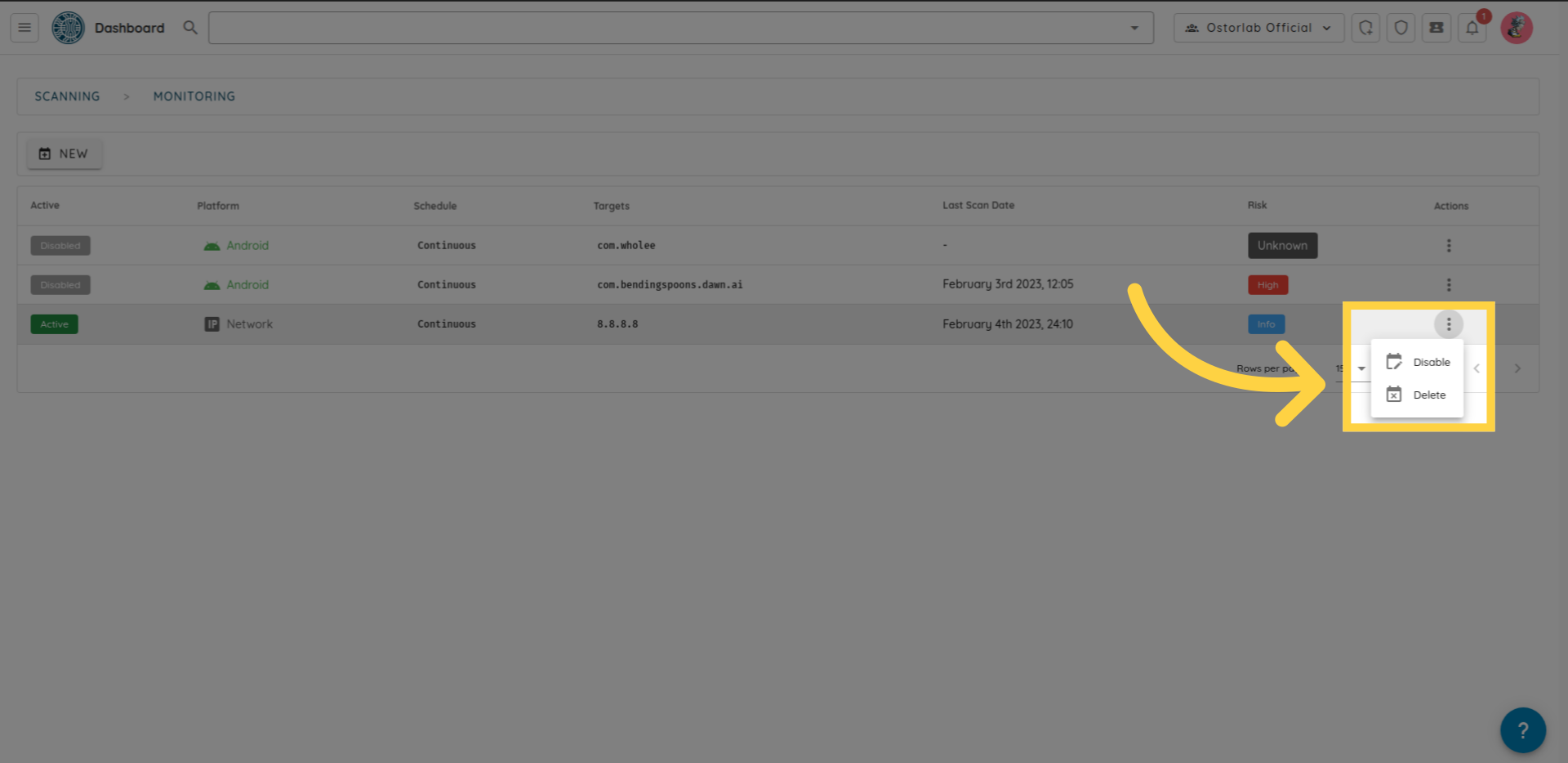
 to enable, disable or delete a rule, click on the three dots on the right.
to enable, disable or delete a rule, click on the three dots on the right.