Saml with OneLogin
This guide walks you through configuring OneLogin as a SAML SSO identity provider (IdP) for Ostorlab.
Prerequisites
Creating the OneLogin Application
The first step is to create a new OneLogin Application for Ostorlab SSO:
- From the OneLogin Administration portal, go to the Applications page and click the Add App button.
-
Search for SAML Test Connector (Advanced) and select it.
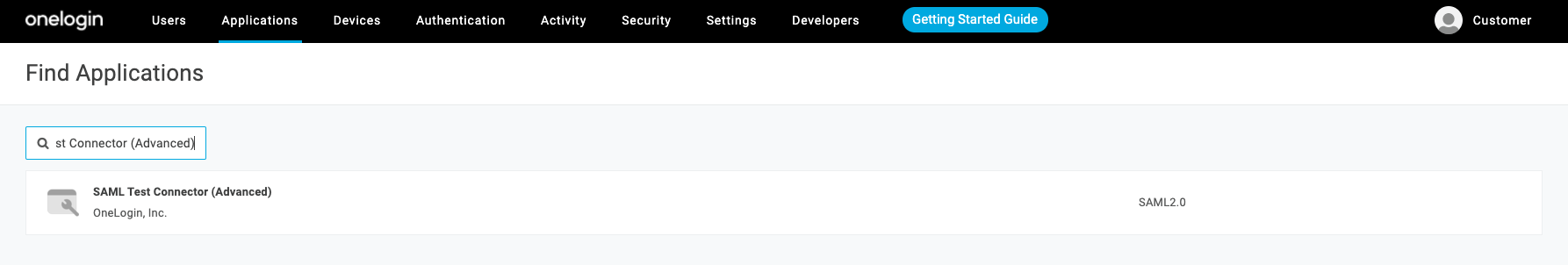
-
Enter a Display Name and optionally a logo.
- Click Save.
Configuring the OneLogin Application
Now configure the OneLogin Application with the SAML settings for Ostorlab SSO
Configure SAML URLs
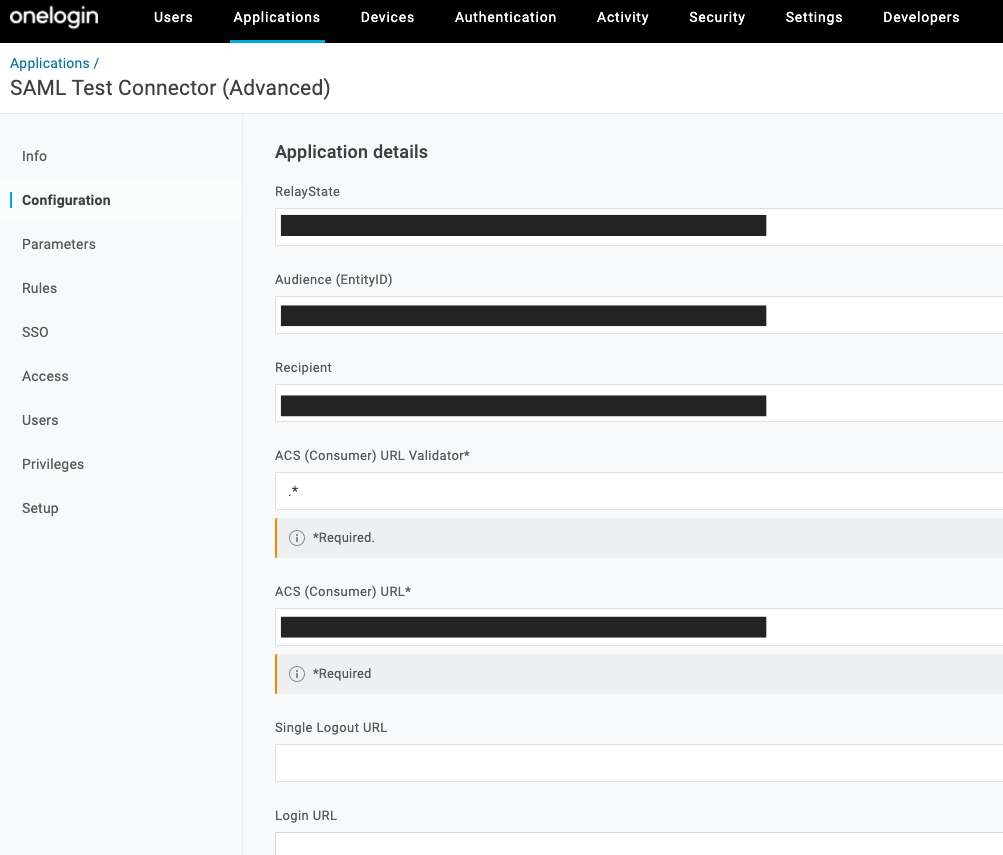
Select the Configuration view for the application and enter/confirm the values in the following table.
Warning: The values you need to use are dependent upon your Ostorlab organisation prefix. Be sure to replace
<organisation_prefix>with your actual organisation prefix. You can find your org’s prefix in your organisation's settings page.
| Configuration Setting | Value |
|---|---|
| Relay State | Empty |
| Audience (Entity ID) | https://api.ostorlab.co/saml/metadata/ |
| Recipient | Empty |
| ACS Consumer URL Validator | .* |
| ACS Consumer URL | https://api.ostorlab.co/saml/acs/?org=<organisation_prefix> |
| SAML initiator | OneLogin |
| SAML nameID format | Email |
| SAML issuer type | Specific |
| SAML signature element | Response |
| SAML encryption method | TRIPLEDES-CBC |
Important: Do not change the value of Name ID Format value once your users have started using Ostorlab—not even switching its value between
EmailAddressorPersistent
Configure SSO Settings
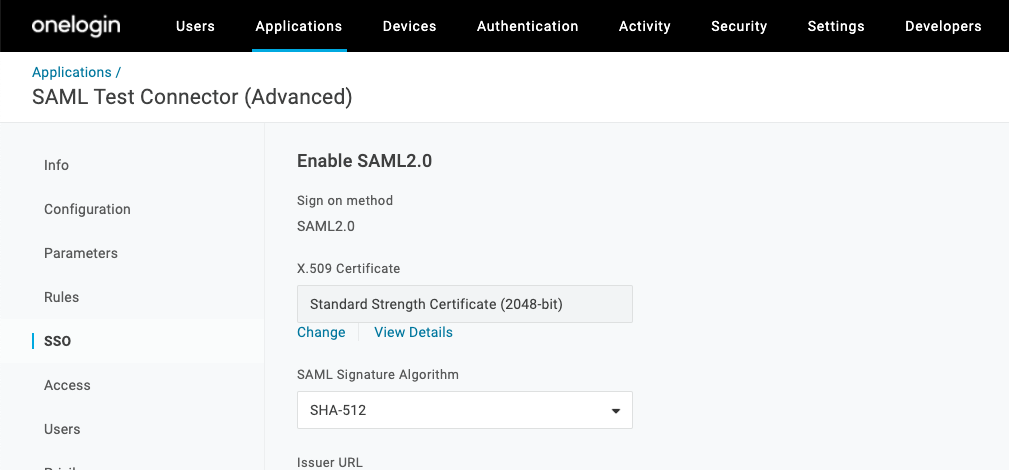
Select the SSO view for the application and set/confirm the following:
| SSO Settings | Value |
|---|---|
| SAML Signature Algorithm | SHA-512 |
User Assignments
After the Ostorlab SAML application has been created in OneLogin, the next step is to assign users to it. This will grant specific users or groups access to sign into Ostorlab with their OneLogin-provided credentials.
To assign users or groups to the application, navigate to the Users tab in the OneLogin portal to add users and then assign them to the Ostorlab SSO application.
Configuring Your Ostorlab Organization
The final step is to configure Ostorlab with details on your new OneLogin-based SAML application. To do this, you need to obtain the IDP metadata document from OneLogin and then provide it to Ostorlab.
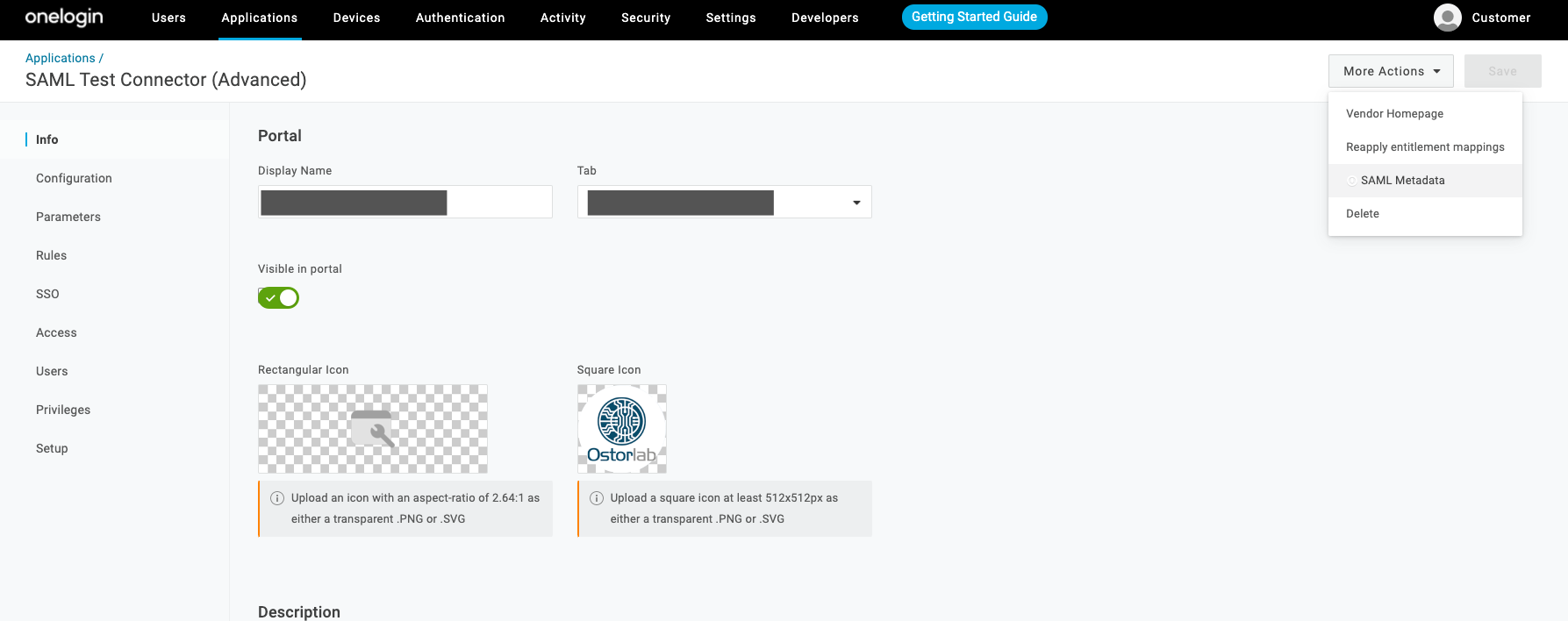
First, navigate to the OneLogin Application you created above and click the More Actions drop down menu button and select SAML Metadata to download the metadata XML file.
- Open the file and copy the entire block of XML text in your clipboard
- Open Ostorlab and navigate to the SAML integration section.
- Select CONFIGURATION.
- Paste the IDP metadata XML into the bottom card titled SAML SSO Settings.
- Click Update.
Once the IDP metadata descriptor has been saved, you are all set to log into Ostorlab.
Signing into Ostorlab with OneLogin
Members of your Google Workspace can now sign into Ostorlab. Navigate to https://report.ostorlab.co/account/login, click LOGIN VIA SSO and enter the prefix of your Ostorlab organisation.