Attack Surface Discovery
What is Attack Surface Discovery / Management?
Attack surface discovery enables continuous monitoring of an organization's infrastructure to detect missing and rogue assets. Coupled with vulnerability scanning it ensures complete coverage of an organization exposure.
Attack surface discovery helps with finding blind spots, common examples are forgotten or missing acquisition infrastructure, unaccounted for dev and production machines or lost assets during internal restructuring and staff change.
Ostorlab's Attack Surface Discovery finds internet-facing assets, be it domains and subdomains, IPv4 and IPv6 addresses,
and Mobile Applications on both Android Playstore and iOS App Store.
Ostorlab's Attack Surface Discovery provides powerful capabilities, including:
- Powerful graph asset correlation that goes beyond subdomain enumeration. Other asset discovery techniques include registry correlation, shallow crawling, shared analytics, reverse lookups, etc.
- Asset Management using a hierarchical ownership model grouped into 4 categories,
Internal,Acquisition,3d Party Service, andExcluded Assets. - Continuous Asset Scanning using either intelligent asset change detection, like a website cache invalidation header, Mobile Application release, or using simple time scheduling CRON rules.
- Powerful Attack Surface visualization to identify asset connections.
- Powerful search and visualization options to zoom in on selected portions of the attack surface or the organization hierarchy.
Finding your Attack Surface
Discovering an attack surface starts by seeding in a list of known assets. This includes IP addresses, domain names, or Mobile Applications. Individual assets can be added or a bulk upload using a CSV file is also possible
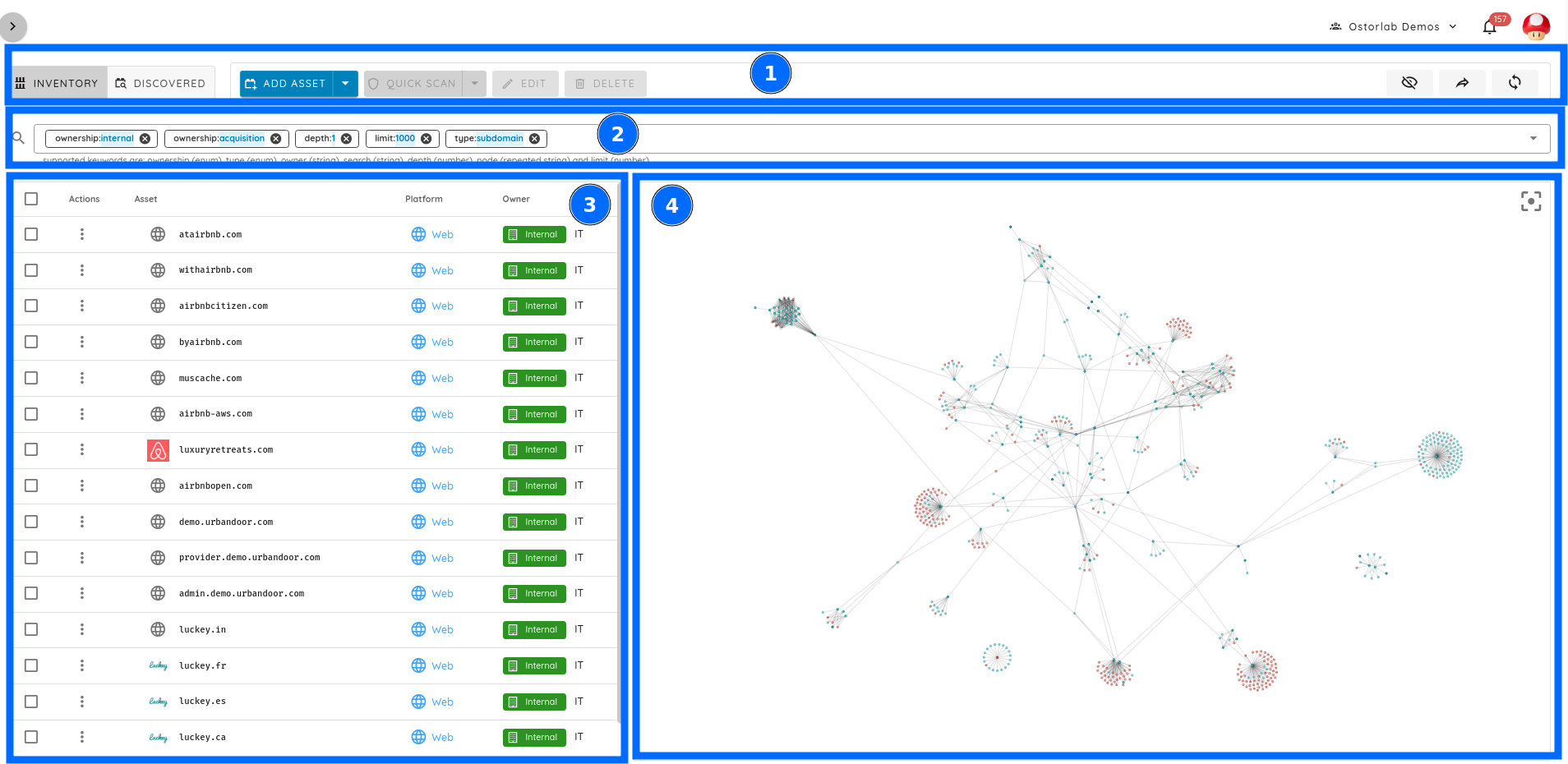
The attack surface page is broken into 4 sections and 2 views:
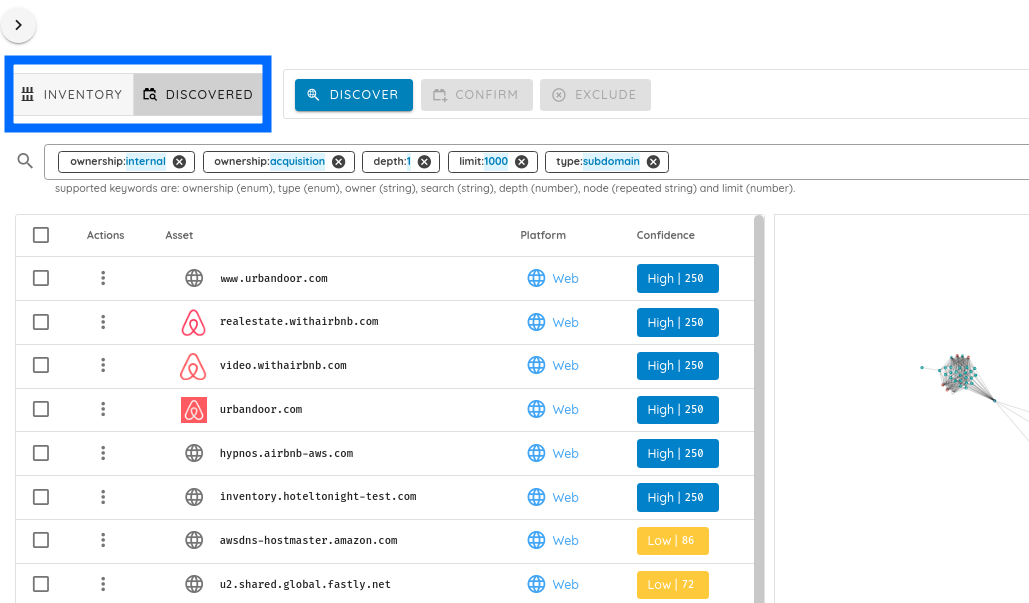
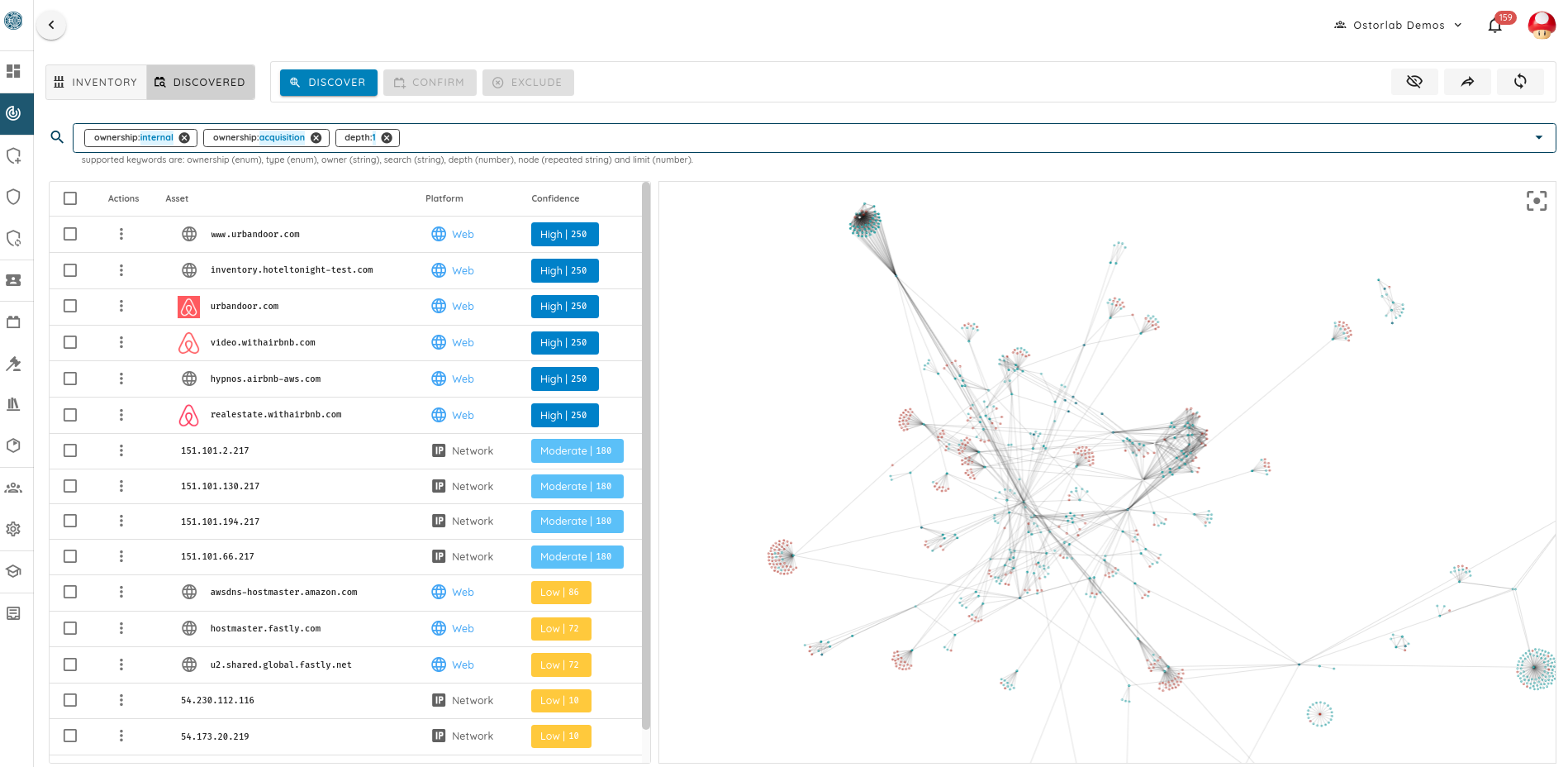
- An actions section to interact with the confirmed and potential assets.
- A search and filtering bar to control what is shown and how it is shown. This bar affects all tables and visualizations in the menu.
- An asset table that can show both confirmed and potential assets depending on the selected mode.
- A visualization menu that shows a graph of assets and their connections in both 2D and 3D modes.
The two views are for confirmed and discovered assets. Switching views affects the actions menu and the assets table.