Saml with Google Workspace (formerly G Suite)
This guide walks you through configuring your Google Workspace (formerly known as G Suite) service as a SAML SSO identity provider (IDP) for Ostorlab.
Prerequisites
Creating the SAML Application
-
In the administrator console for your Google Workspace domain, open the flyout menu in the upper-left corner and choose Apps > Web and mobile apps.
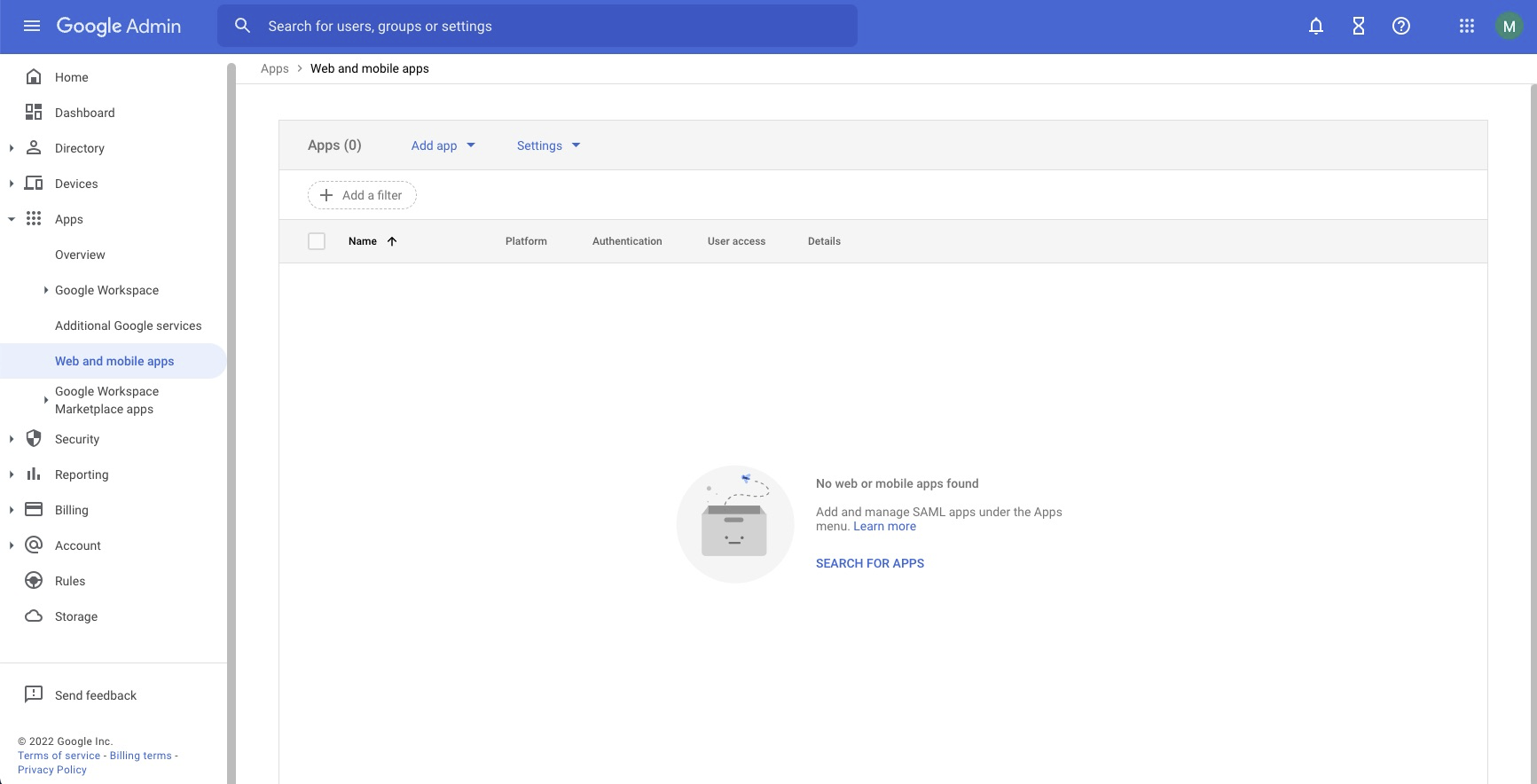
-
Select Add app > Add custom SAML app to create a new SAML application.
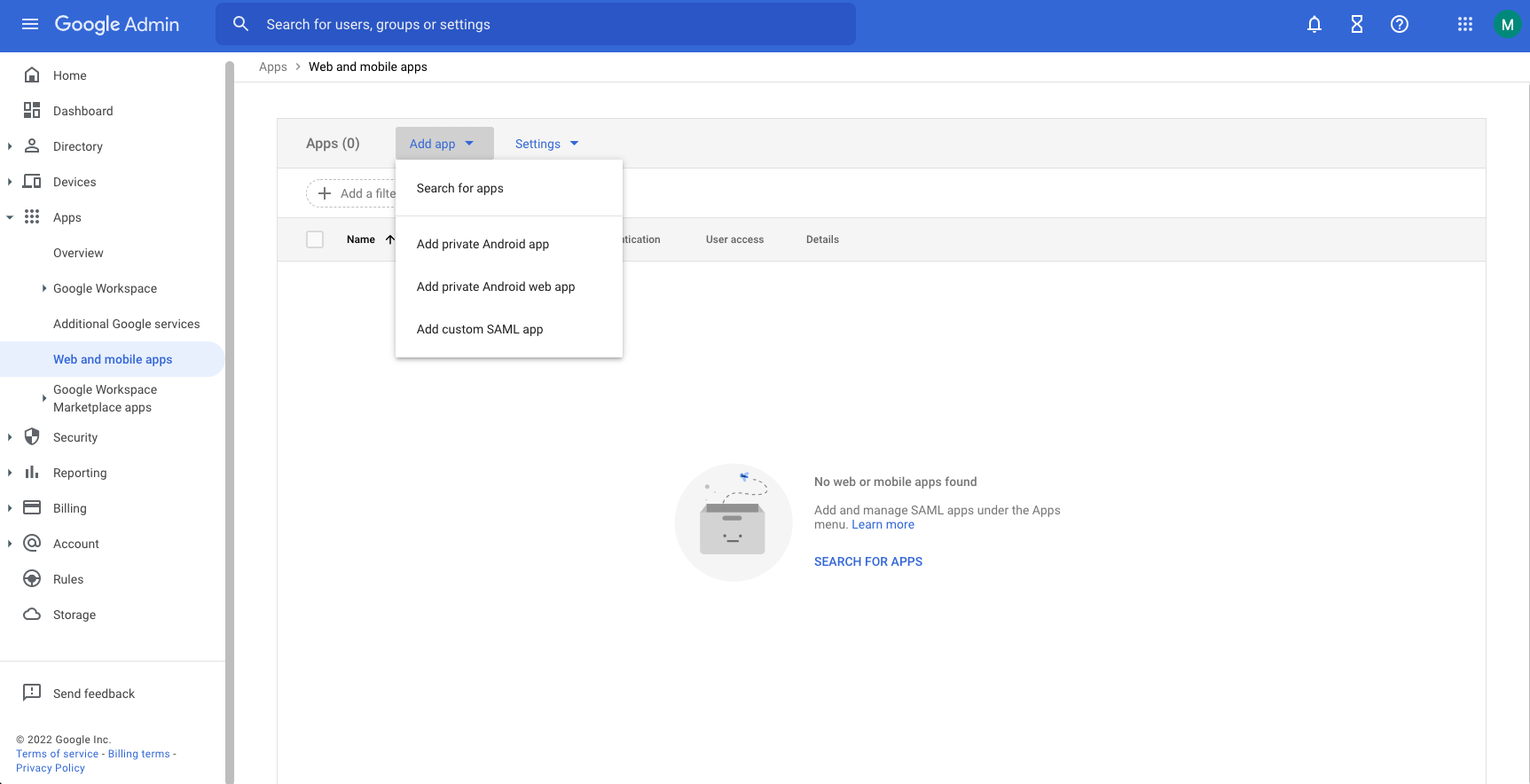
-
In the first step, give the SAML app a name (e.g., Ostorlab-SSO), and optionally add an App Icon, and select Continue.

-
Next, choose Option 1: Download Metadata to download an XML document that identifies and describes your Google Workspace domain as a SAML identity provider. You will need this document to complete the process of configuring your Ostorlab organisation. For now, note the location of the downloaded file, then select Continue to continue.
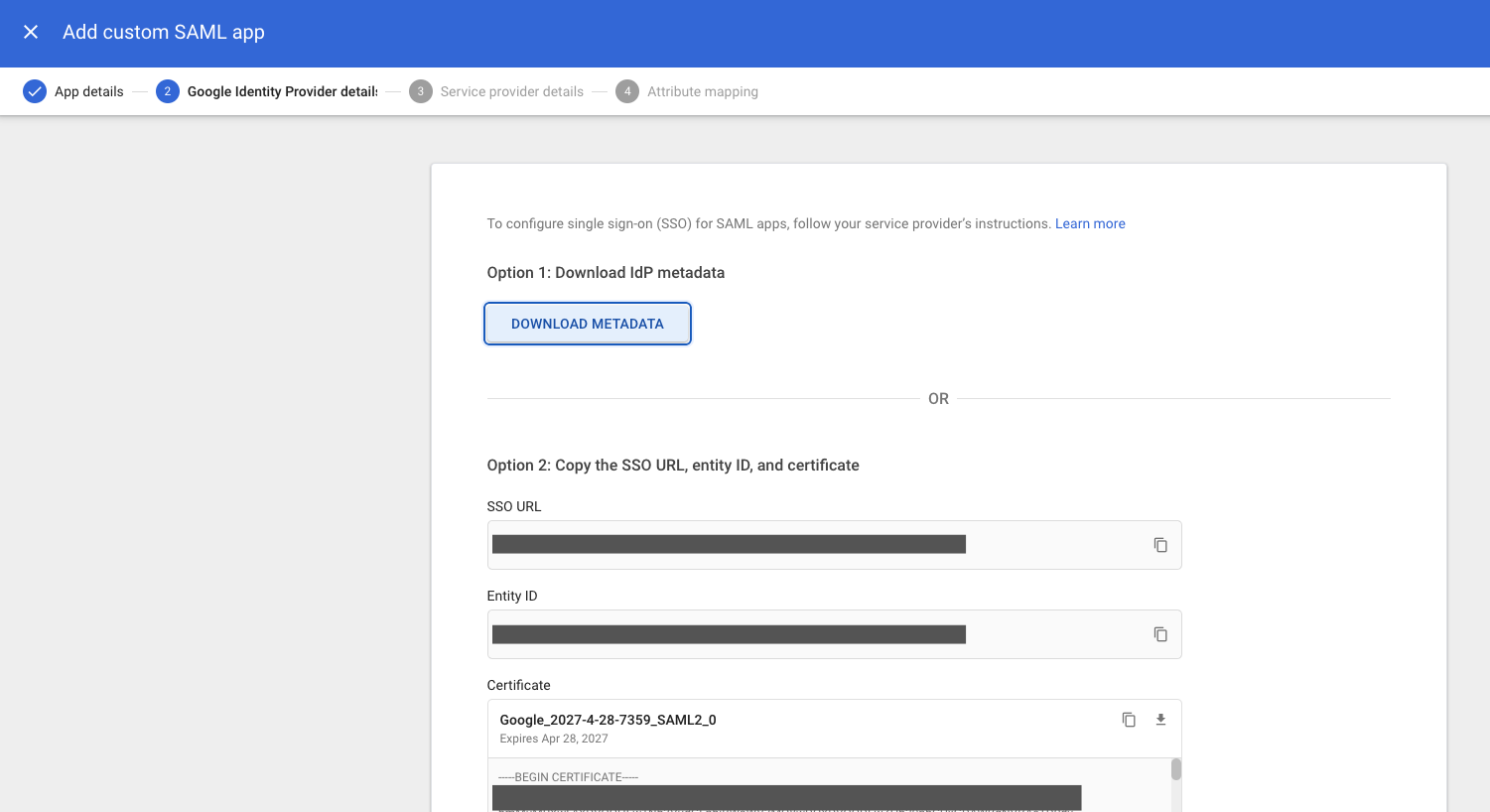
-
In step 3, for the required ACS URL and Entity ID and Start URL fields, enter the fully-qualified URLs of the acs and metadata and sso endpoints of the Ostorlab API, adjusted for your Ostorlab organisation name.
Warning: The values you need to use are dependent upon your Ostorlab organisation prefix. Be sure to replace
<organisation_prefix>with your actual organisation prefix. You can find your org’s prefix in your organisation's settings page.
| SAML Setting | Value |
|---|---|
| ACS URL | https://api.ostorlab.co/saml/acs/?org=<organisation_prefix> |
| Entity ID | https://api.ostorlab.co/saml/metadata/ |
| Start URL | Empty |
| Name ID Format | urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST |
| Assertion Consumer Service Binding | urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified |
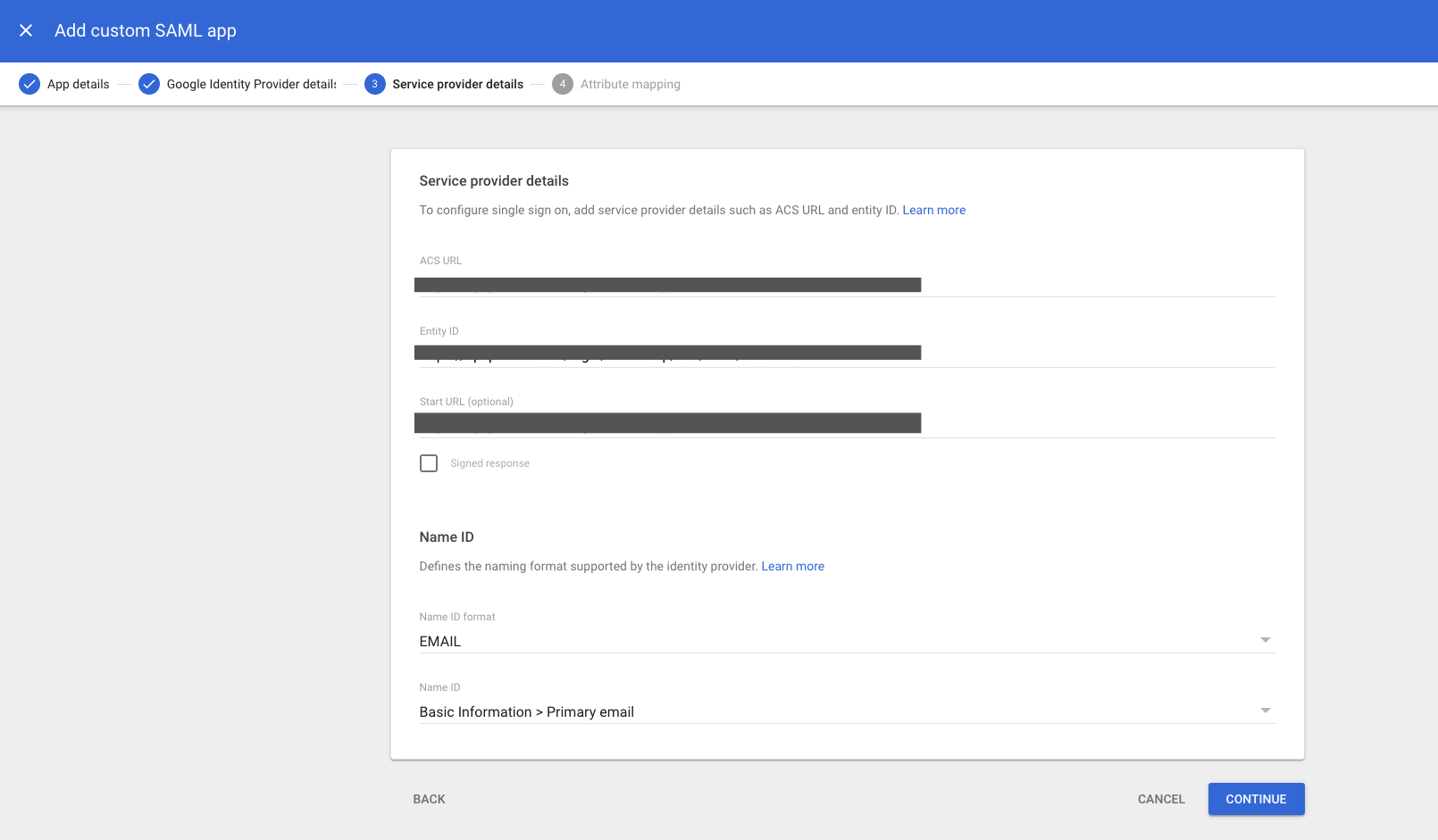
Leave the other fields as their default values, then select Continue.
Important: Do not change the value of Name ID Format value once your users have started using Ostorlab—not even switching its value between
PERSISTENT
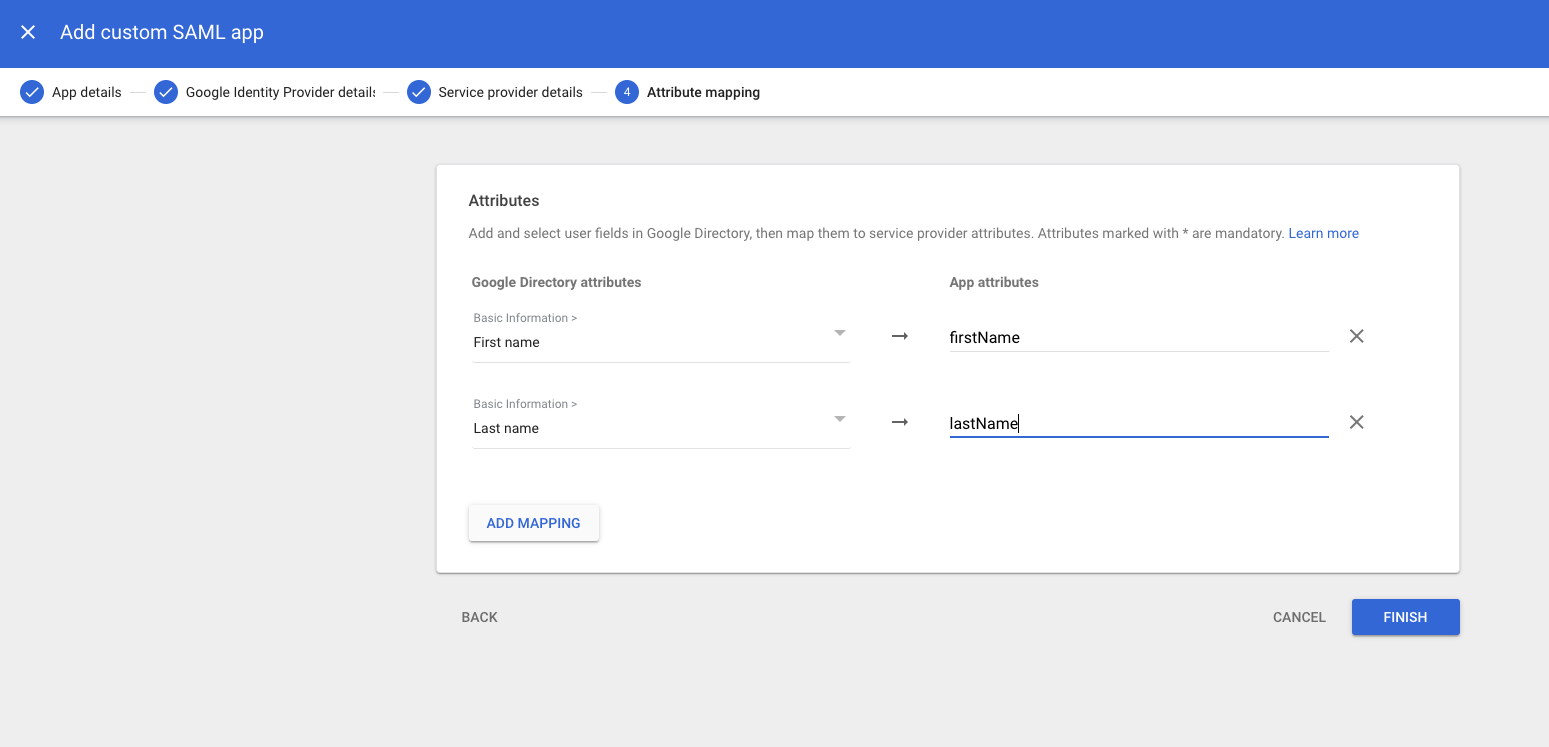
- The final step—attribute mapping—is optional, but you may wish to specify proper first and last names for your Ostorlab users, based on their Google account profiles. Ostorlab expects to receive these fields as
firstNameandlastName, respectively.
Once you add them, select Finish.
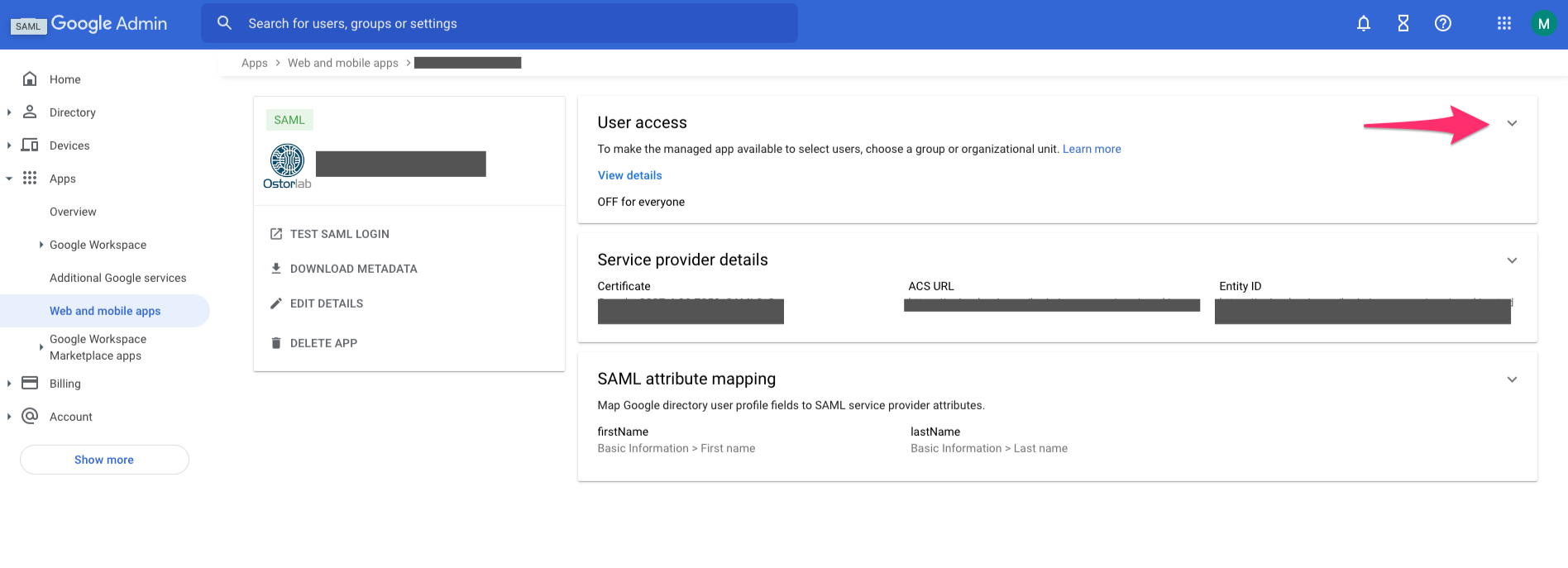
- On the next screen, enable your newly created SAML application for your Google domain users by selecting the down arrow in the User access panel:
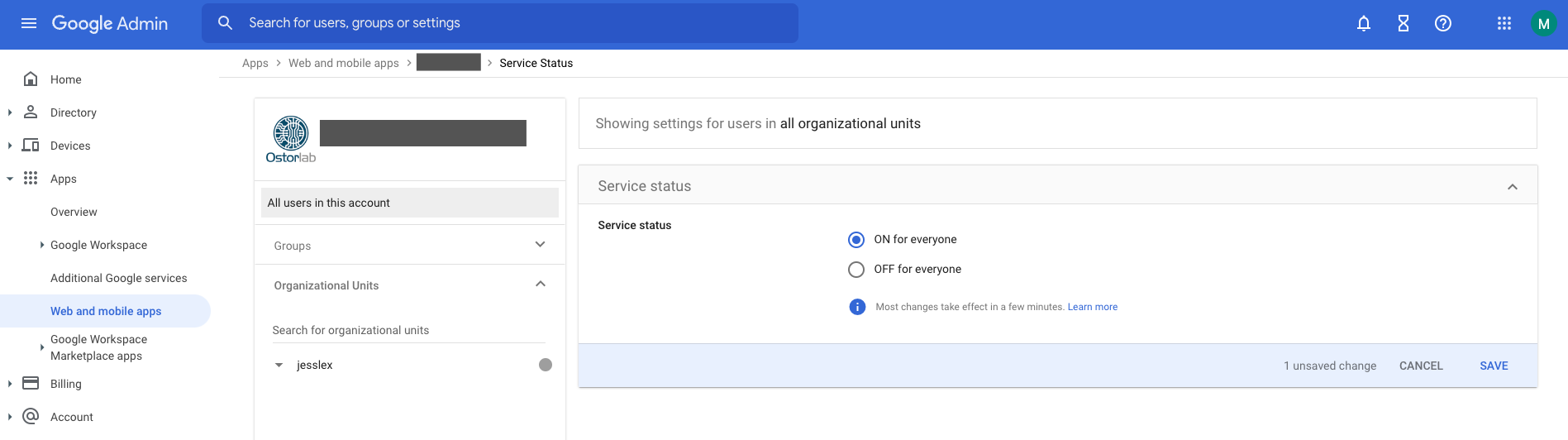
Select ON for everyone and Save.
At this point, you’re done configuring Google Workspace, and can move on to completing SAML SSO setup in Ostorlab.
Configuring Your Ostorlab Organisation
The final step in the process consists of associating your Ostorlab organisation with your SSO identity provider.
- Sign into Ostorlab and navigate to the SAML integration section.
- Paste the full contents of the XML IDP document you have previously downloaded into the text box.
- Select Update
Your Ostorlab organisation is now configured to use Google as a SAML SSO identity provider.
Signing into Ostorlab with Google
Members of your Google Workspace can now sign into Ostorlab. Navigate to https://report.ostorlab.co/account/login, click LOGIN VIA SSO and enter the prefix of your Ostorlab organisation.
Troubleshooting
Google Workspace SAML troubleshooting page: SAML app error messages